Alice’s Yard Stick ♠️🔶❤️🔎 Part 2
The surveillance state continued…
Welcome back to part 2 of Alice’s Yard Stick. In this series, I continue to cover the non-exhaustive list of how the public and private sector violates the privacy of every day Americans. If you missed the first post, you can go back and read it here.👇👇👇👇👇
Alice’s Yard Stick ♠️❤️🔶🔎
“Those who would give up essential liberty to purchase a little temporary safety, deserve neither liberty nor safety.”
Your Thoughts 🧠
Demonstration of Voice to Skull remote 65 kilohertz Modulated signal, which enables voices to be beamed into someone’s mind.
Source ~RedPillb0t
Your Autonomy 🤖
Source: TheSCIF
Your Location 🗺️
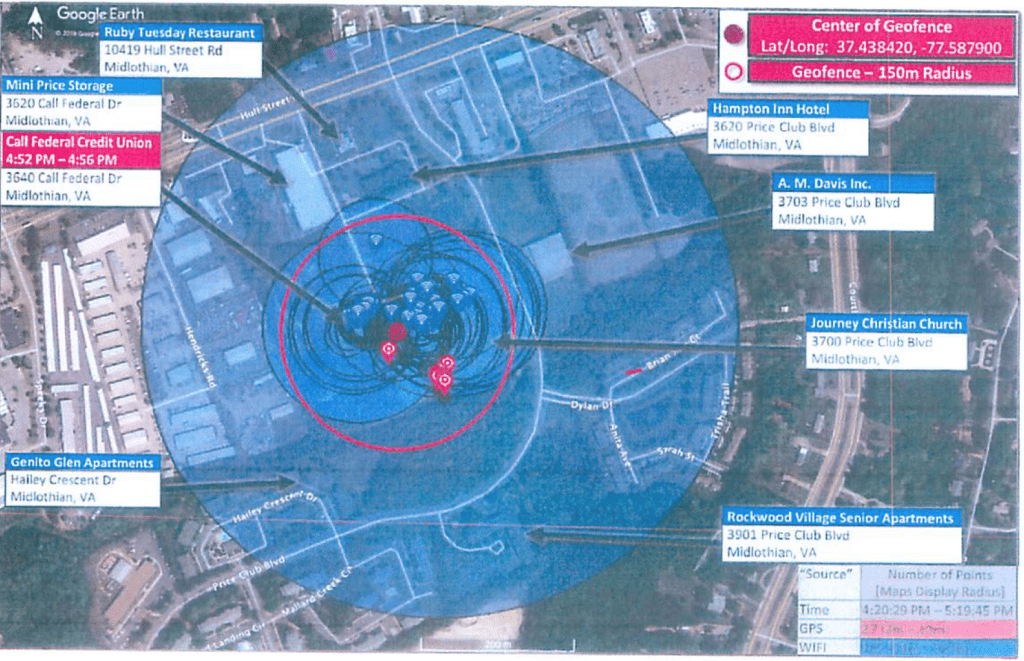
Geofence Warrants (Reverse location warrant)
A geofence warrant (also called a reverse location warrant) is a court order that compels a company to search its database for all mobile devices that were within a defined geographic area during a specified time window not tied to a known suspect.
Imagine this: Police have no suspect in a crime, no witnesses, no footage. They draw a virtual fence around the crime scene on a map and a specific time window. Then they ask Google (or other tech companies) for every phone that was inside that fence during that window.
That’s a geofence warrant (aka reverse location warrant).
How It Works
Cops get court approval for the geofence boundaries & timeframe.
Google searches its massive Location History database (from apps, GPS, Wi-Fi, etc.).
It returns an anonymized list of devices (dots on a map) that were there often dozens or hundreds.
Investigators pick the most suspicious patterns and request user identities (names, emails) for those few.
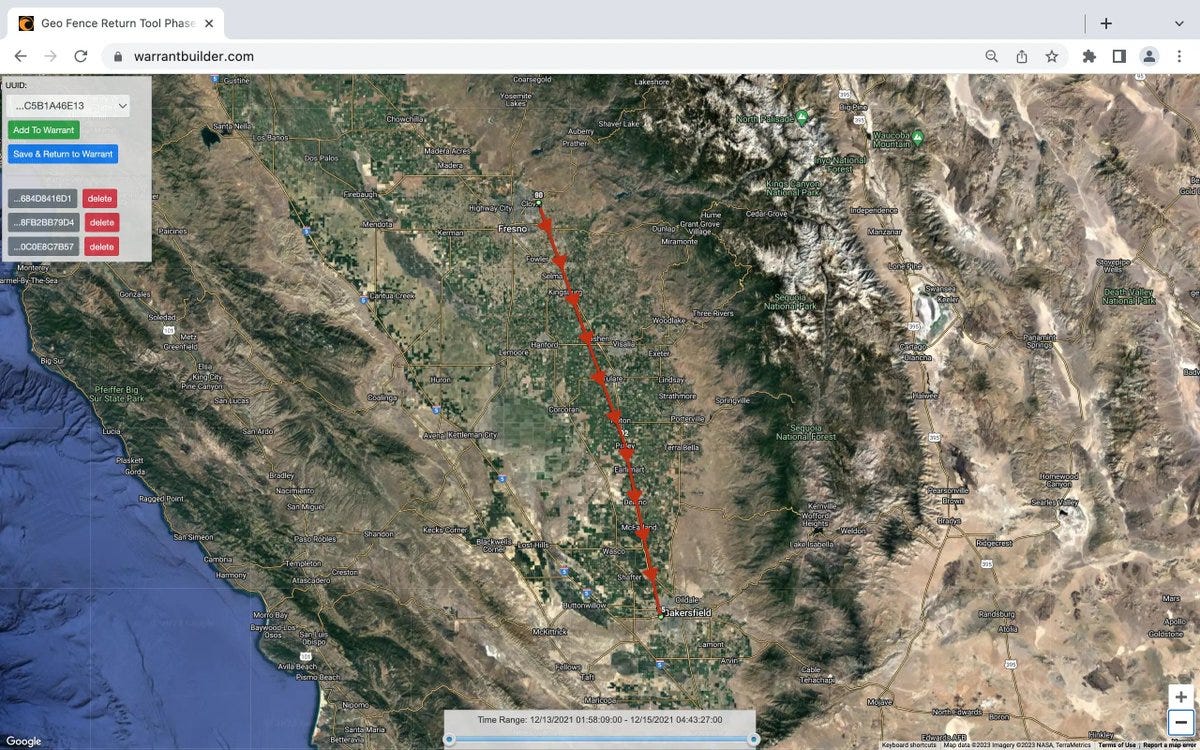
Here are real examples of what these geofence maps look like when police narrow down devices:
SOURCE: T3chfalcon
Your Mind🧠
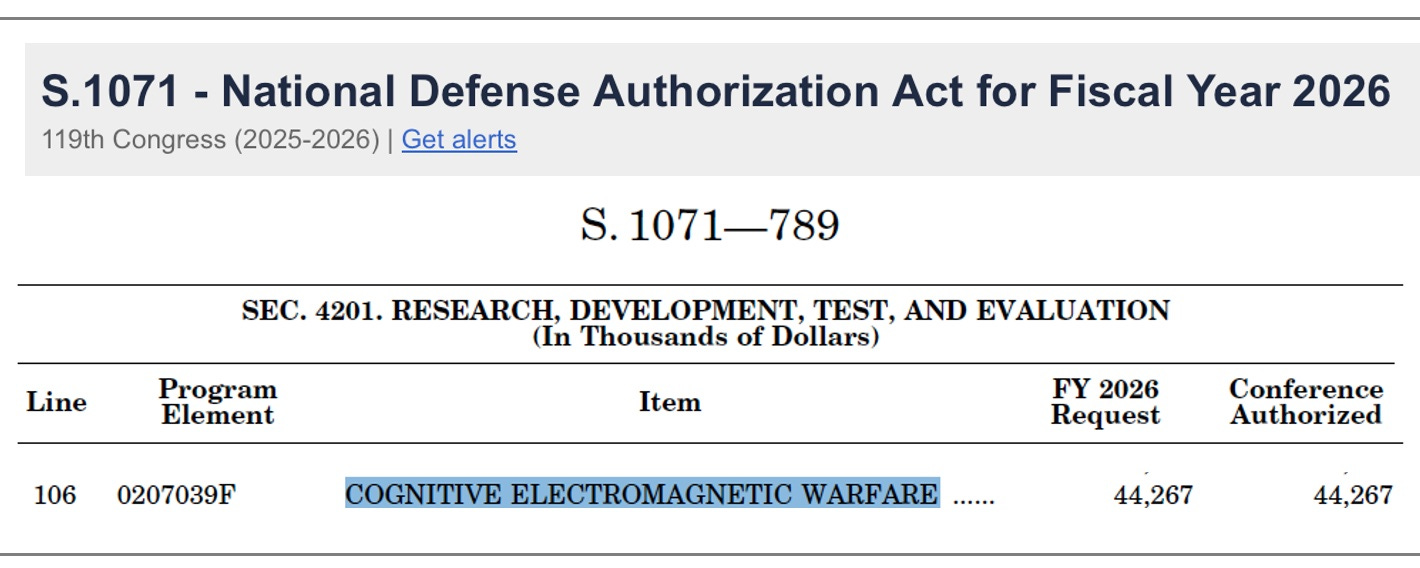
Cognitive Electromagnetic Warfare
It’s real. Here’s a line item in the NDAA.
SMS Messages 📲
The Silent SMS is one of the creepiest surveillance tricks nobody talks about.
No sound or popup.
Not even a message.
Your phone simply gets a hidden ping.. and it quietly replies.
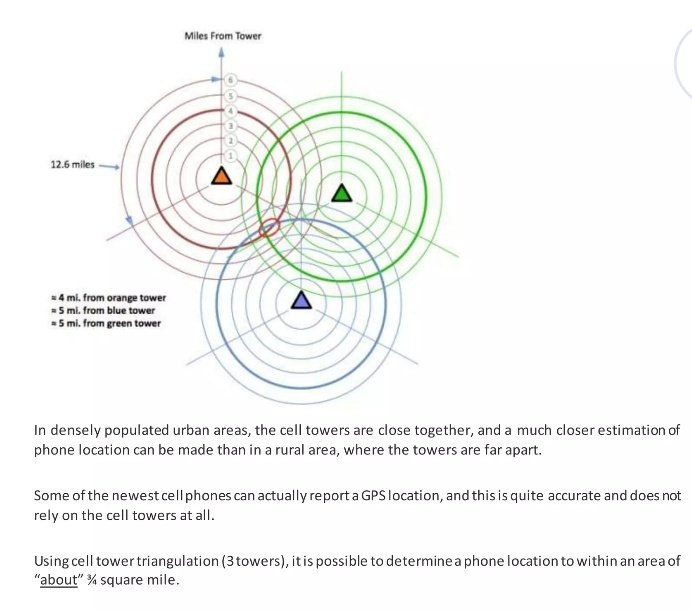
That reply forces your phone to talk to the nearest cell tower, updates your real-time location, and confirms you’re active.
Law enforcement has used it for years.
And NO you can’t stop it.
SOURCE: T3chfalcon
In the next post, I will share a new “Privacy-Focused” mobile carrier which eliminates many of the surveillance vulnerabilities common mobile carriers have. If you need privacy, this new startup is worth trying. Stay tuned